If you were running servers in the 2000s, you probably remember the constant struggle against worms, botnets, and distributed-denial-of-service (DDoS) attacks.
It was a wild, dangerous time for anyone hosting applications online.
Fast forward to today, and cloud computing, rate limiting, firewalls, and modern security tools have revolutionized how we defend against DDoS attacks and API abuse.
But how did we get here?
1. The Chaos of the 2000s: How DDoS Attacks Worked
1.1 The era of open Security holes and Kitchen computers with Public IP address’s..
Back in the early 2000s, if you wanted to host a website or a remote server, you often got a static IP from your ISP.
Nerds like me would host Apache servers, remote desktops, and game servers from our home connections.
Usually a PC we bought at Costco with a Celeron processor, that we set up in the bedroom or a corner of the kitchen… :)
Operating Systems (Windows Especially) had alot more security holes back then , and automatic system updates was not as much of a thing as it is now..
As time went on and more and more people got online..
All these people online combined with the huge number of unexploited security holes (in Windows mostly) , created fertile ground for hackers, botnets and viruses..
Common Hacker\botnet attack methods in the 2000s:
- Exploiting Windows security holes to install bots
- Scanning IP ranges to find unprotected home servers
- Hacking routers and firewalls to access private networks
- Using worms like Blaster to infect as many machines as possible
1.2 Personal Experience-The Blaster Virus
In 2005, I was in San Diego Data Center deploying a Enterprise Pharmacy System my Team and I built for a Major Supermarket Chain when Blaster hit.
(Yes we went to the datacenter back then - physically- to install web applications. The software engineering team and I had to physically install the new servers.. and install windows etc… )
Blaster was insane.. it hit the world HARD…
Blaster (computer worm) - Wikipedia
The Most Famous Virus in History: Blaster
The Most Famous Virus in History: Blaster
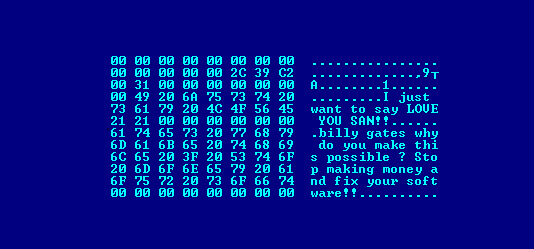
“”""
This worm came from United States on August 11, 2003, and only affected computers with operating systems that had Windows 2003/XP/2000/NT.
Blaster contained the message in your code: “I just want to say I love you San!” (We still do not know who San is) and added, “Billy Gates, why do you make this possible? Stop making money and fix your software “.
""""
Blaster hit us hard.. it took- literally- several days to get to a point where we had working laptops and working servers..
Blaster was VERY infectious.. And when it hit your computer it slowed to a crawl making removing the virus take forever.. it would spread on a network very quickly…
Blastor was a self-replicating worm that spread via an unpatched Windows vulnerability.
🔴 Blaster’s impact:
- Infected machines slowed to a crawl
- Clicking “Start Menu” took 1-2 minutes to load
- Computers would randomly crash and reboot
- Downloading the Blaster removal tool was nearly impossible because the infection spread faster than people could fix it
Blaster was a VERY Motivating Incident which cause all of us in the industry to change how we thought and change how we wrote software and secured networks.
1.3 The Rise of Botnets and DDoS Attacks
Once a hacker infected enough machines, they created a botnet—a network of compromised devices waiting for commands.
🔹 How hackers launched DDoS attacks in the 2000s:
- Infected thousands of PCs worldwide
- Waited for an instruction from the hacker
- All infected PCs sent HTTP requests to a website
- Overloaded the website’s servers, crashing them
Example attacks that Happened:
- Yahoo (more popular than Google at the time) was taken down by botnets
- Buy.com, eBay, CNN, Amazon.com, ZD-Net, E-Trade were also taken down
- Small businesses (like mine) with 20-100 servers were crippled
- Home web servers running on DSL/cable modems were easily overwhelmed
""""
- In February 2000, some of the Internet’s most reliable sites were rendered nearly unreachable by distributed denial-of-service (DDoS) attacks. Yahoo! took the first hit on February 7, 2000. In the next few days, Buy.com, eBay, CNN, Amazon.com, ZDNet.com, E-Trade, and Excite were taken down by DDoS attacks. Though damage estimates vary widely, the FBI estimates that the companies suffered $1.7 billion USD in lost business and other damages.
<Timeline of Internet conflicts - Wikipedia>
""""
1.4 “Slashdot Effect”: A Non-Malicious DDoS
Another common issue in the 2000s was “slashdotting” or “The Slash Effecr—when a popular website (like Slashdot) linked to a small blog.
🔹 What happened?
- Thousands of people clicked the link at the same time
- The tiny home server running Apache collapsed
- Website became unusable for hours/days
Although not intentional, it was still a denial-of-service attack.
These problems led to modern rate limiting, request filtering, and cloud security tools.
Slashdot effect
With that background, know you know the history and the concepts.
Lets look at some simple defenses and how to set them up .
1.5 API Rate Limiting: The First Line of Defense
API rate limiting controls the number of requests a client can send within a certain time.
🔹 How rate limiting stops modern DDoS attacks:
- Limits requests per second per IP
- Prevents bots from sending too many requests
- Protects servers from getting overwhelmed
Example: Rate Limiting in NGINX
| |
Apply:
| |
Now, each IP can only send 60 requests per minute, preventing abuse.
1.6 Web Application Firewalls (WAFs)
Web Application Firewalls (WAFs) filter and block malicious requests.
🔹 How WAFs stop attacks:
- Block SQL injection, cross-site scripting (XSS), and bot traffic
- Detect unusual traffic patterns
- Automatically ban abusive IPs
Example: WAF in AWS
| |
1.7 Distributed Denial-of-Service (DDoS) Protection
The major Cloud providers offer built-in DDoS protection.
🔹 Examples of modern DDoS protection tools:
- AWS Shield
- Google Cloud Armor
- Azure DDoS Protection
- Cloudflare (edge protection for websites)
These absorb attack traffic before it reaches your server.
1.8 Today vs the 2000s..
✅ Problems We Solved
- Windows security holes are patched faster
- Firewalls and routers are more secure
- Botnets are harder to build (due to auto-updating OSes)
- Rate limiting and filtering stop most DDoS attempts
❌ Problems That Still Exist
- Ransom DDoS attacks (RDDoS)—attackers demand payment to stop attacks
- IoT botnets—millions of unpatched smart devices are vulnerable
- AI-powered attacks—bots are getting smarter at bypassing security
We still need constant security updates, advanced AI detection, and proactive defense strategies.